BlackHat MEA 2023 - vec
The vulnerability is in this part, we can bypass the if statement by integer overflow. Therefore, we are able to achieve out-of-bounds writing in the heap area.
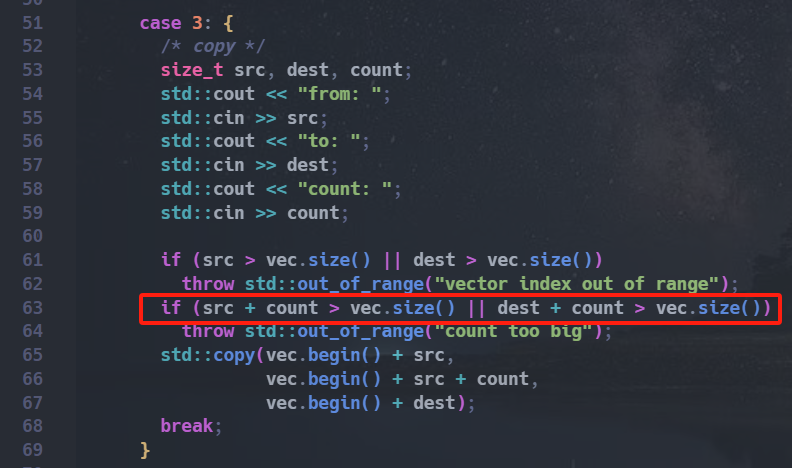
Step 1, leak the heap address. The vector of template class will allocate for twice the current memory size when the current memory is not enough. In the first two times, it will ask for 8 bytes and 16 bytes of memory from the heap allocator, which will return a chunk of size 0x20(In the following text, we refer to them as chunk a and chunk b). Then, when it allocate memory for the third time, it will get a chunk of size 0x30(chunk c) and the two previous chunk will be freed into the tcachebins(0x20). Now we can use chunk c to read and write the data in chunk a and chunk b. At this step, we can leak the heap address and hijack the fd pointer of chunk b to the victim chunk d(will be introduced in the following). For the convenience of next exploitation, we also need to modify their size to prevent them from being placed on the tcachebins(0x20) or tcachebins(0x30).
Step 2, leak the libc address. Repeatedly calling the vector’s emplace_back function until it can allocate for an unsorted chunk(chunk d). Then put chunk d into unsortedbin and calling the vector’s clear function. At this point, when the vector tries to allocate memory next time, it will ask for 8 bytes of memory just like the beginning. Because the fd pointer of chunk a has been hijacked, so we will get chunk d when the vector allocates memory for the second time. After that, we can exploit the vulnerability again to leak the libc address on chunk d.
Step 3, leak the stack address. After the first two steps, this step will appear relatively simple. We just need to call the vector’s clear function and return to the first step situation. Allocate for two chunks of size 0x20(chunk e and chunk f) .Then hijack the fd pointer of chunk f to the address of environ(a variable on libc that stores stack address). Calling the vector’s clear function again and we can get a fake chunk which points to environ at the next two allocations of vector. And then we can leak the stack address on the environ variable.
Step 4, hijack the execution flow of the program. Reuse the process from step 3 and allocate the stack address which stores the retaddress of main function. Finally, building our ROP chain on the stack to hijack the flow of execution to system(“/bin/sh”).
PS
- We should make sure that the size of fake chunk is valid because the destructor of vector will be called before the main function returns.
- The fake chunk address should be near the target address (above or below) because we will pollute the data on the target address when exploiting the vulnerability, which can lead to unexpected errors.
exp
1 | #!/usr/bin/python2 |
This is my first time writing a blog in English, so there might be some parts that are not very fluent to read. Please bear with me.
