Grey CTF 2024 - Heap Heap Heap
1st place〜^^
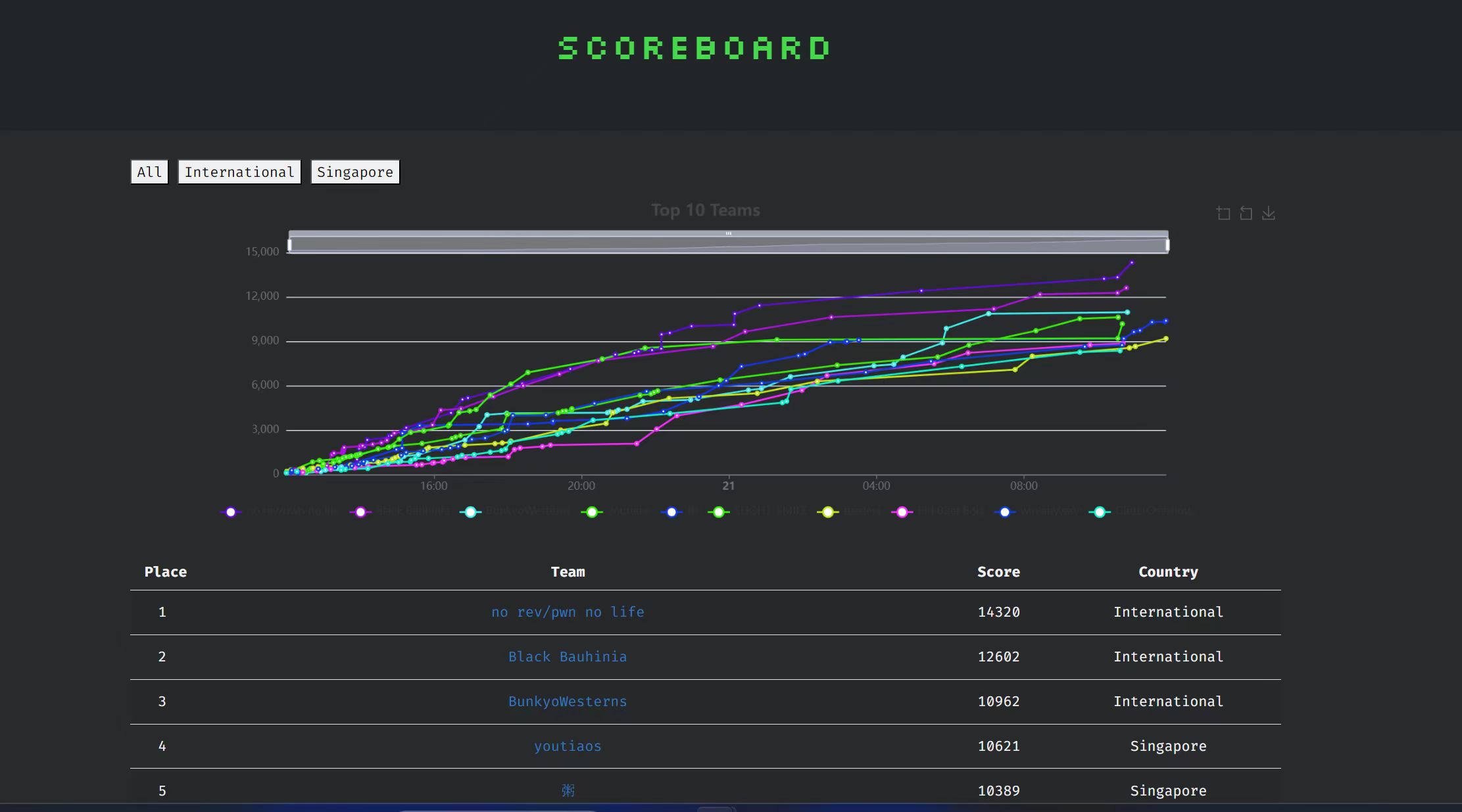
Heap Heap Heap (2 solves)
We can bypass the check for memory_needed > heap_heap.top_size via integer overflow vulnerability of statement struct Node *node = heap_heap.top in function halloc. This can help us leak the memory address and do the next step of exploitation.
After we leaked the base address, we can use the integer overflow vulnerability of statement struct Node *new_node = node->data + size to achieve arbitrary memory allocation the next time we allocate a node using halloc. In my solution, I make the new_node to a nearby address of heap_heap structure so that I can control the structure, which makes the rest of exploitation easy.
Continue, we just need to hijack the heap_heap.top to the GOT of exit then allocate a node with size of the address of function backdoor. The GOT of exit will be assigned to backdoor in the statement node->value = size. Finally, enter 4 to choose the exit option of the menu and it will trigger the backdoor through exit.
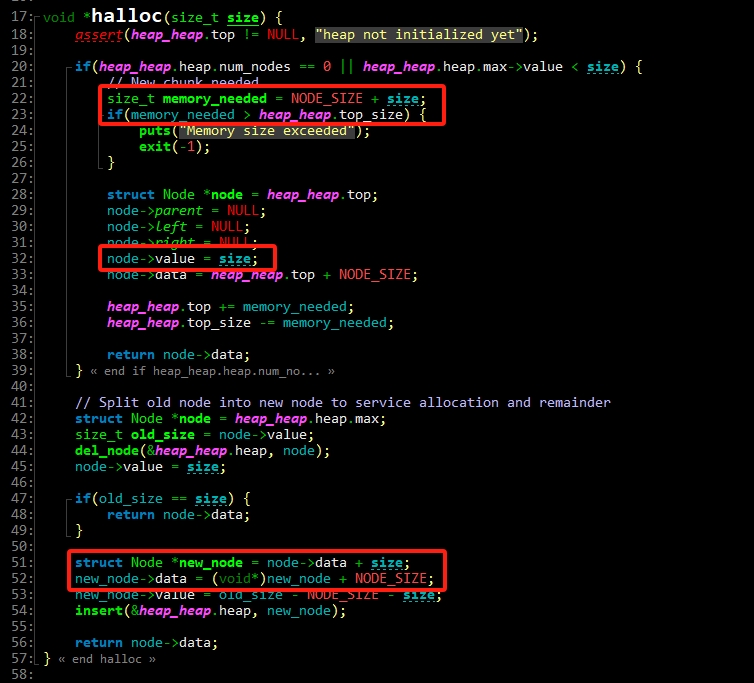
PS: After sharing my solve script and discussing with the author of the challenge in the Discord channel once the contest was over, it seems my approach wasn’t the intended solution :)
1 | #!/usr/bin/python2 |
